Our Technology
Your intelligence engine
Speed, depth, and clarity—no other credit intelligence and data provider comes close. At Octus, real-time data and insights fuel your decision-making. Octus is your definitive edge in a competitive landscape, transforming complex information into your next strategic move. We architected superior technology not just to set us apart, but to put you ahead.

100k+
client's credit related queries answered
12,000
CreditAI users
5,000+
source data documents and content
Built by experts. Enhanced by AI. Engineered for you.
Where human insight meets machine intelligence
Octus technology is forged from the real-world experience of more than 150 technologists—experts in everything from cybersecurity and data engineering to artificial intelligence—all focused to serve our clients and to revolutionize credit market intelligence.
Video credit: Permira. View the full feature.
At the forefront of credit intelligence
We are constantly pushing the envelope, asking, ‘What if we could do this faster? Smarter?’ This relentless drive led to CreditAI by Octus®. Launched in 2023, it’s the first client-facing GenAI tool that truly transforms how credit information is understood, acting as the intelligence front-end for the market’s only truly unified credit platform.

Breaking the speed barrier to break the news faster
The results are not just incremental; they are transformative. Our proprietary data technology, fine-tuned by our data and editorial teams, has enabled us to publish content 50% faster with 99% accuracy. It’s this seamless tandem of human expertise and technological might that allows us to manage 6 million documents across 40,000 deals, turning a world of complexity into your single source of clarity.
Driving differentiated covenants data
Octus is the premier provider of innovative covenant solutions. By bringing together Octus’ market-leading human expertise from our team of senior finance lawyers and advanced AI, Octus Deal Term Analytics provides deep, reasoned insights on document data and covenant queries.
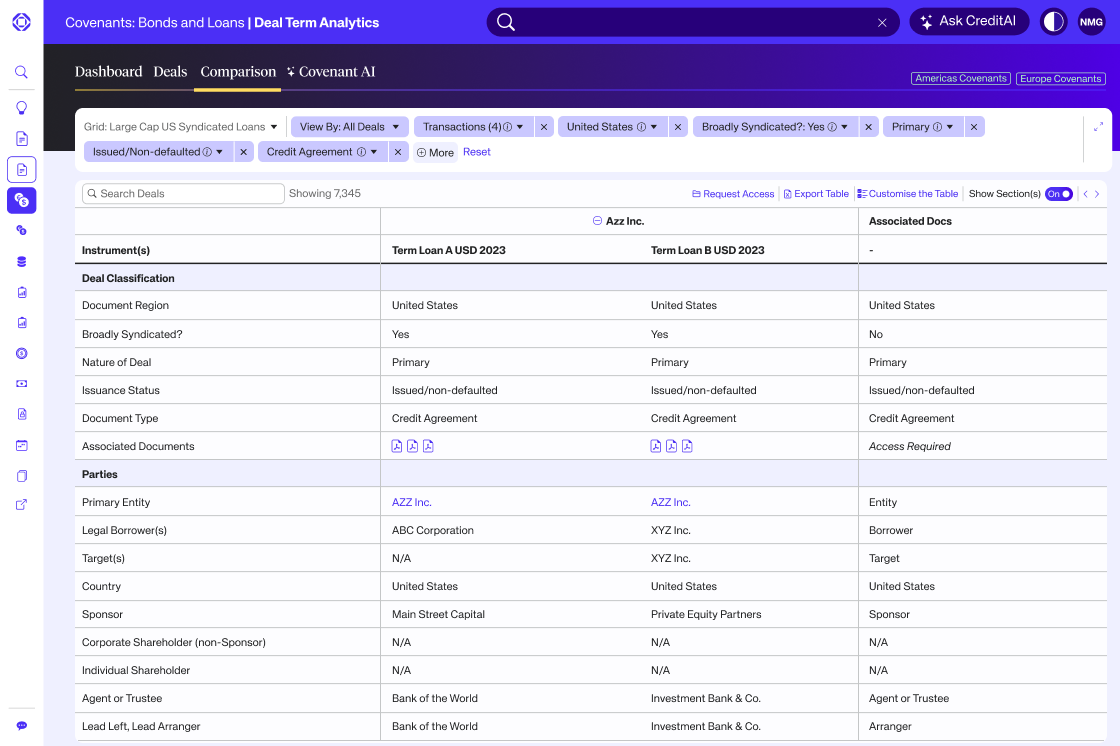
Sophisticated delivery. Instant Insights.
At Octus, we believe in simplifying access to critical information. Octus Direct Data Services is designed to provide seamless, local access to data developed by our team of 300+ market experts. By integrating internal and third-party sources into one connection, we enable you to focus on what matters—analyzing and acting on insights when you need them.

Revolutionary Platform for Credit Managers
Sky Road, the credit portfolio management solution from Octus, offers investors exceptional usability and performance for managing all types of credit vehicles and strategies, by integrating portfolio management, optimization, compliance, trade order management and research management workflows.
Engineered for what’s next
Our platform isn’t just robust; it’s built for the speed of the market. Leveraging premier cloud-native infrastructure, we deliver institutional-grade performance, scalability and resilience. This is the operational backbone that ensures our clients have critical intelligence the moment they need it, without compromise.
Scalable
Octus technology is designed to meet the complex demands of enterprise-level firms. Our architecture can adapt to growing data volumes from various sources and scale exponentially.
Efficient
Our AI-integrated software analyzes vast datasets, identifies patterns and provides actionable insights, optimizing workflows and boosting efficiency.
User-centered
Our subscriber-centric design adapts to individual needs, offering customizable interfaces and workflows, with API-led connectivity.
Powerful
Our centralized data pipeline consolidates diverse data sources into a unified, powerful repository.
Integrated
Octus technology ensures rigorous data governance, eliminates silos and delivers data consistency.
Secure
Octus cybersecurity operates at enterprise scale, consistently adapting to safeguard data and systems, foster innovation and maintain trust.
IT Security: The Foundation of Trust at Octus
In an industry where data breaches cost an average of $6 million per incident and cyberattacks have surged 25%1 year-over-year, one metric stands out at Octus: zero security incidents affecting customer data.
The catalyst: AI-integrated intelligence
When it comes to AI, Octus takes a more human approach. This means integrating AI to amplify human capabilities and expertise, not to replace it. Delivering superior value to clients, AI is deeply integrated and ethically and responsibly woven into every facet of our operations.
A universe of insight
We ingest and synthesize a colossal scope of information—from public and private market data to filings, transcripts and exclusive sources. But data is only potential. Our strength lies in transforming that potential into power. With powerful AI capabilities, we don’t just collect information; we structure the unstructured, connecting disparate points to reveal a single, coherent picture of opportunity and risk.
From data to decision
Where others see complexity, our AI sees patterns. We move beyond simple automation. Our proprietary AI and machine learning models are trained by market experts to think like market experts. They don’t just find data points; they surface actionable intelligence, predict trends, and identify critical signals hidden within the noise. This is how you get to the ‘why’ faster than anyone else.
Intelligence with integrity
As data science experts, Octus is pioneering the future with a commitment to responsible innovation. Our AI is built on a strict ethical framework, ensuring that every insight is not only powerful but also transparent, explainable and free from bias. We believe the greatest advantage is one you can trust completely.
Security, compliance and governance
In our world, security is not a feature; it is the foundation. We employ a rigorous, multi-layered security protocol, architected from the ground up to protect your data and our intelligence as the mission-critical assets they are. We don’t just meet industry standards; we aim to set them. With SOC 2 Type II certification and a culture of continuous auditing, we ensure our operations, data handling, and infrastructure are held to the highest possible measure.
Award-winning technology. Purpose-built performance.
Our awards tell a simple story: technology that works. We’re honored to be recognized by industry leaders for transforming how data is delivered, analyzed, and acted on — with precision, speed, and impact.
Octus data principles – AI and security framework
At Octus, our commitment to security, compliance and ethical AI is absolute. We provide the intelligence and data our clients need to act with total confidence.
These FAQs outline key data principles, including the robust frameworks that underpin our technology and protect our clients, subscribers, and business partners.
FAQs: Security and Vulnerability Management
Security is not just a feature; it is the foundation of our platform. We implement a multi-layered security strategy to protect client data and ensure system integrity.
Our security framework is built on six foundational pillars, each reinforced by advanced AI to enhance speed and accuracy:
- Cloud Security: We continuously monitor our cloud environments to prevent misconfigurations and secure our infrastructure.
- Application Security: Security is integrated directly into our software development lifecycle, protecting against vulnerabilities in both our code and open-source libraries.
- Identity & Access Management: We enforce centralized, strict control over employee and customer access, ensuring permissions are appropriate and immediately revoked when no longer necessary.
- Endpoint & Workforce Security: All company devices are hardened, encrypted, and equipped with remote wipe capabilities. We pair this with strong email security and mandatory workforce training to mitigate human-error risks.
- Threat Detection & Response: Our systems and networks are monitored 24/7 by our security partner, to rapidly identify and contain potential threats.
- Compliance & Governance: We maintain SOC 2 certification and conduct rigorous vendor reviews to manage supply chain risk and provide assurance to our clients and partners.
- Encryption: All client data is protected with strong encryption, both at rest and in transit.
- Access Control: We enforce multi-factor authentication (MFA) for all administrative access and utilize a role-based access control scheme to ensure access is restricted to authorized personnel.
- Threat Detection: We use a threat detection monitoring tool for continuous network oversight. System firewalls are configured to limit unnecessary ports and protocols.
- Code and Data Security: We have a strict source code management protocol with access controls and automated security scans. Our databases are configured with role-based permissions and encryption.
- Employee Security: All employees and contractors undergo background checks and are required to complete annual information security and awareness training.
AI is a critical component of Octus’ security program, enhancing our ability to protect our systems with greater speed and precision. We use AI to:
- Detect misconfigurations and risky changes in our cloud environment.
- Review code continuously to surface high-impact vulnerabilities.
- Analyze access patterns to detect anomalies and automate the rightsizing of permissions.
- Identify phishing attempts and device anomalies that may be missed by human review.
- Correlate signals across systems for faster, more accurate threat alerts.
Our proactive approach to security includes:
- Implementing the NIST Secure Software Development Framework (SSDF).
- Conducting thorough security testing and code reviews during the development lifecycle.
- Implementing strong input validation to prevent common attacks like SQL injection.
- Regularly monitoring for new and emerging AI-specific threats.
- Applying the principle of least privilege to limit the potential impact of any compromise.
Yes. Our threat detection and response capability includes 24/7 Security Operations Center (SOC) coverage through a third party.
We have also implemented automation to respond immediately to security alerts—such as disabling a compromised account or isolating a device—reducing our response time from hours to minutes.
Octus has successfully completed a SOC 2 Type II attestation, covering the systems and processes that support FinDoxTM and the Octus AI platform, a testament to our commitment to security and data protection. We have also adopted multiple frameworks from the National Institute of Standards and Technology (NIST) to align our security program with global best practices, including:
- NIST Cybersecurity Framework (CSF)
- NIST Secure Software Development Framework (SSDF)
- NIST AI Risk Management Framework (AI RMF) (Deployment in Q1 2026)
FAQs: Compliance, Data Privacy & Ethical AI
We are committed to upholding the highest standards of data privacy and regulatory compliance, ensuring our clients can trust our platform completely.
Octus adheres to comprehensive compliance and regulatory standards across all aspects of our business, including federal securities laws, anti-corruption regulations (FCPA), data privacy requirements, employment law, and accounting standards.
We maintain rigorous information barriers to ensure equal market access, strict internal controls to prevent insider trading, and ethical business practices in all our operations.
Our Compliance framework is designed to protect our customers, maintain the integrity of our data and insights, and ensure we operate with the highest standards of regulatory adherence and transparency.
Protecting client data is paramount. Our data privacy measures are governed by strict contractual provisions and internal policies.
- Data Isolation: We isolate each client’s information through logical separation, and where appropriate, physical separation, such as maintaining client-specific vectorized databases in CreditAI use cases.
- Data Anonymization: Data is anonymized before being used for training or operational purposes.
- Strict Access Controls: We implement and enforce strict, role-based access controls to restrict access to sensitive data.
- Data Use Limitation: Data is never used or disclosed to third parties outside the scope defined in our client agreements.
- Regular Audits: We conduct regular audits of our data security practices to identify and address potential vulnerabilities.
Our ethical framework is built on eight essential pillars that guide the development and deployment of our AI solutions:
- Fairness: Designing solutions to eliminate bias against individuals or groups.
- Transparency: Providing stakeholders with a clear understanding of what is happening in each AI solution.
- Explainability: Ensuring solutions can answer how and why a conclusion was reached.
- Accountability: Embedding human oversight and responsibility across the AI lifecycle.
- Data Integrity: Acquiring and using data in compliance with all applicable laws and assessing it for accuracy and quality.
- Reliability: Ensuring AI solutions operate consistently and precisely as intended.
- Security: Implementing robust practices to safeguard AI solutions against malicious actors or adverse events.
- Safety: Designing and implementing AI to safeguard against harm to people, businesses, and property.
Join us
Looking for a career-defining role in technology?


